3 min to read
Setting up ArgoCD SSO with GitLab
A comprehensive guide to implementing ArgoCD SSO with GitLab
Overview
In the last post, I tried configuring ArgoCD SSO using Google Oauth,
This post explains how to configure Single Sign-On (SSO) for ArgoCD using GitLab. We’ll walk through the process of setting up GitLab OAuth and integrating it with ArgoCD.
Prerequisites
- GitLab instance
- ArgoCD installed on a Kubernetes cluster
- Administrative access to both GitLab and ArgoCD
Steps
1. Create GitLab Application
- Navigate to Admin Area > Applications in GitLab
- Create new application:
- Name: Argo CD
- Redirect URI: https://argocd-server-urlapi/dex/callback
- Select Scopes:
- read_user
- openid
- profile
- Save the credentials:
- Application ID (Client ID)
- Secret (Client Secret)
2. Configure ArgoCD Installation
Create values/mgmt.yaml:
global:
domain: argocd.your-domain.com
configs:
params:
create: true
server.insecure: true
ssh:
extraHosts: |
gitlab.concrit.us ssh-rsa AAAAB3N...
gitlab.concrit.us ecdsa-sha2-nistp256...
gitlab.concrit.us ssh-ed25519 AAAA..
controller:
replicas: 1
dex:
enabled: true
redis:
enabled: true
server:
replicas: 1
ingress:
enabled: true
annotations:
nginx.ingress.kubernetes.io/force-ssl-redirect: "false"
nginx.ingress.kubernetes.io/ssl-passthrough: "false"
ingressClassName: "nginx"
path: /
pathType: Prefix
repoServer:
replicas: 1
applicationSet:
replicas: 1
notifications:
enabled: true
3. Configure GitLab SSO
Update values/mgmt.yaml with SSO configuration:
configs:
cm:
timeout.reconciliation: 60s
dex.config: |
connectors:
- type: gitlab
id: gitlab
name: GitLab
config:
baseURL: <gitlab url>
clientID: <application id>
clientSecret: <secret>
redirectURI: https://<argocd url>/api/dex/callback
groups:
- server
rbac:
create: true
policy.csv: |
p, role:org-admin, applications, *, */*, allow
p, role:org-admin, clusters, get, *, allow
p, role:org-admin, repositories, *, *, allow
p, role:org-admin, projects, get, *, allow
p, role:org-admin, logs, get, *, allow
p, role:org-admin, exec, create, */*, allow
g, <group>, role:org-admin
secrets:
dex.gitlab.clientId: "<application id>"
dex.gitlab.clientSecret: "<secret>"
Apply the changes:
helm upgrade argocd . -n argocd -f ./values/mgmt.yaml
kubectl rollout restart -n argocd deployment argocd-dex-server
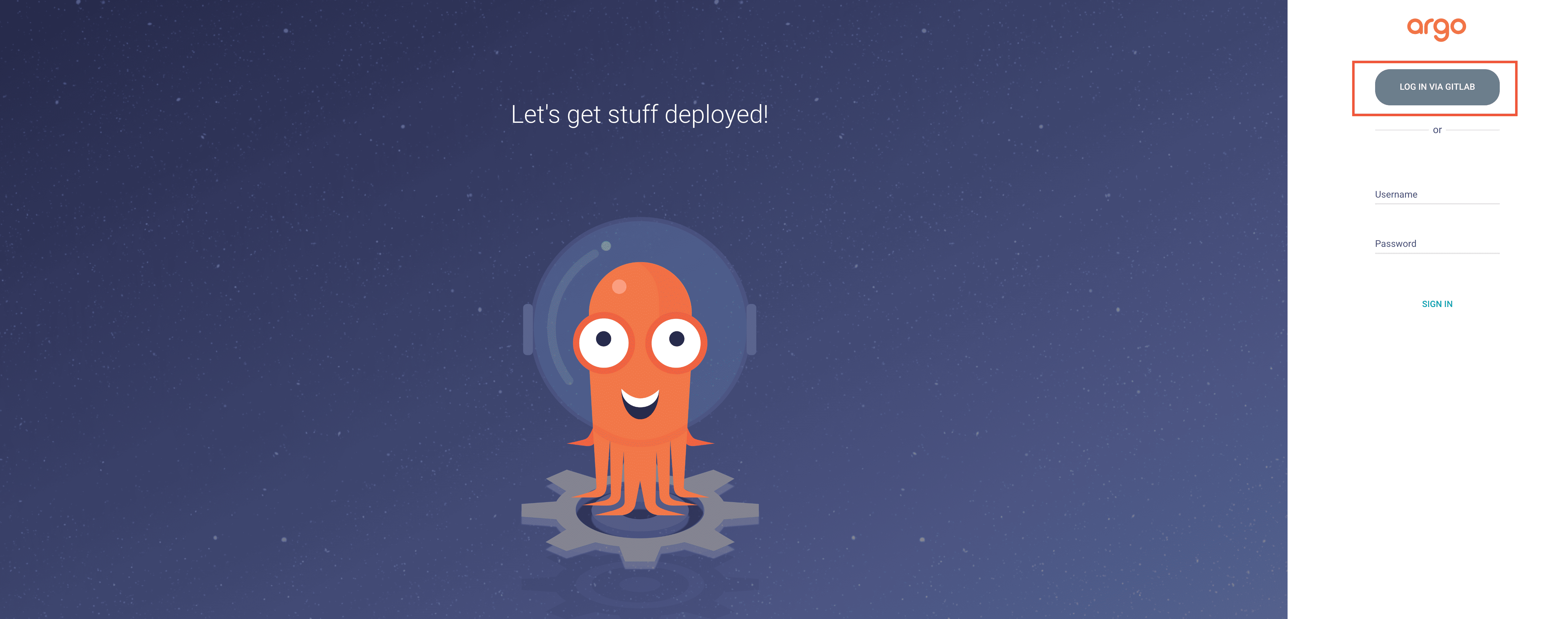
4. Test Login
Access your ArgoCD instance and verify GitLab SSO login works correctly.
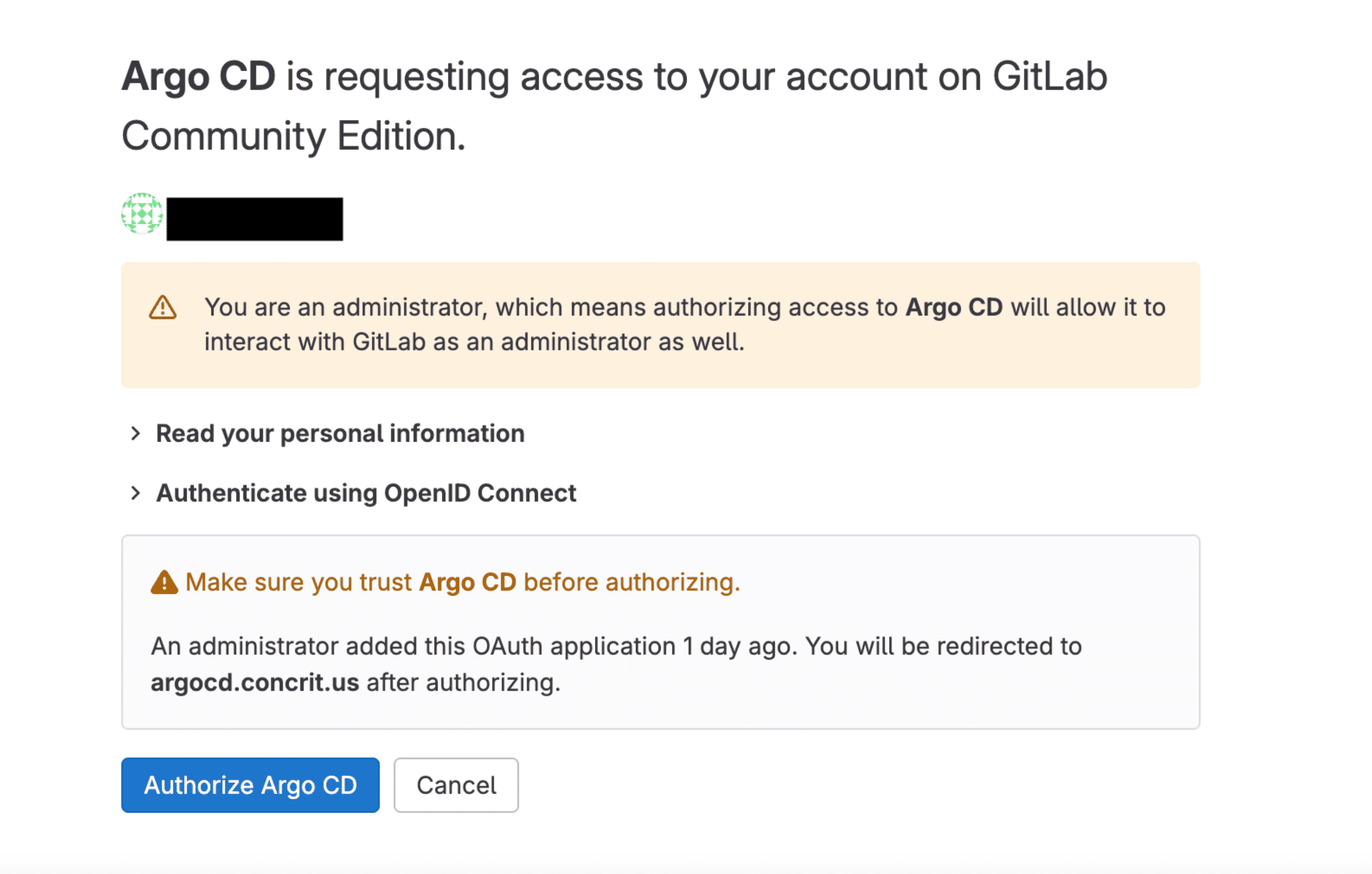
Authentication Processes
- OAuth Authentication
- SAML Authentication
- OpenID Connect Authentication
- Consider domain settings, security policies, and network configurations
- Keep up with the latest documentation as GitLab and ArgoCD settings may change
- Ensure proper backup before making configuration changes
- Key points for SSO configuration:
- dex.config: Authentication configuration
- rbac: Permission settings
- Proper mapping between GitLab groups and ArgoCD roles

Comments