2 min to read
Single Sign-On (SSO)
A comprehensive guide to SSO and authentication protocols
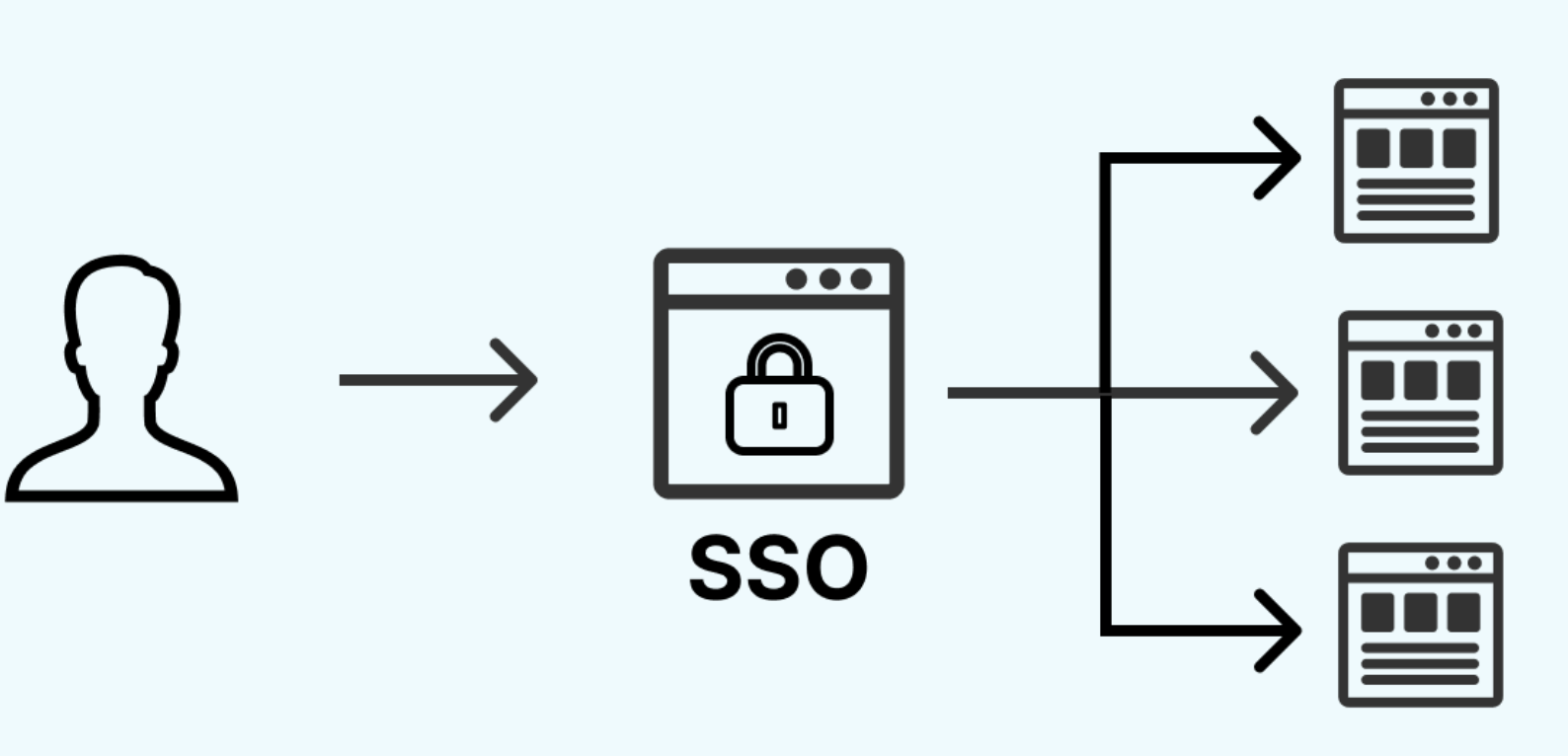
Overview
Single Sign-On (SSO) enables users to access multiple systems with a single authentication process.
What is SSO?
SSO is an authentication scheme that allows users to access multiple applications with one set of credentials. It:
- Improves user experience
- Reduces authentication complexity
- Enhances security
- Centralizes access management
Key Benefits
1. Enhanced User Experience
- Single login for multiple services
- Reduced password management
2. Improved Security
- Centralized authentication
- Stronger password policies
3. Efficient Resource Management
- Centralized user management
- Simplified administration
Authentication Protocols
OAuth (Open Authorization)
Purpose:
- Delegation of access rights
- Third-party application authentication
- API authorization
Operation:
- Token-based authentication
- Resource owner authorization
- Defined access scopes
sequenceDiagram
participant User as User
participant ClientApp as Client Application
participant AuthServer as Authorization Server
participant ResourceServer as Resource Server
User->>ClientApp: Request access to resource
ClientApp->>AuthServer: Redirect user for authentication
AuthServer->>User: Authenticate and grant permission
AuthServer-->>ClientApp: Return authorization code
ClientApp->>AuthServer: Exchange auth code for access token
AuthServer-->>ClientApp: Access token
ClientApp->>ResourceServer: Request resource with access token
ResourceServer-->>ClientApp: Return resource
SAML (Security Assertion Markup Language)
Purpose:
- Enterprise SSO
- XML-based framework
- Identity provider communication
Operation:
- IdP authentication
- SAML assertions
- Service provider validation
sequenceDiagram
participant User as User
participant ServiceProvider as Service Provider
participant IdentityProvider as Identity Provider
User->>ServiceProvider: Access request
ServiceProvider->>User: Redirect to IdP for SSO
User->>IdentityProvider: Authenticate (if not already)
IdentityProvider-->>ServiceProvider: SAML Assertion (authentication response)
ServiceProvider->>IdentityProvider: SAML Assertion
ServiceProvider-->>ServiceProvider: Validate Assertion and create session
ServiceProvider-->>User: Access granted
OIDC (OpenID Connect)
Purpose:
- Identity layer over OAuth 2.0
- User authentication
- Profile information access
Operation:
- JWT-based ID tokens
- OAuth 2.0 extension
- RESTful implementation
sequenceDiagram
participant User as User
participant ClientApp as Client Application
participant OpenIDProvider as OpenID Provider
User->>ClientApp: Request login
ClientApp->>OpenIDProvider: Redirect user to OP
OpenIDProvider->>OpenIDProvider: Authenticate
OpenIDProvider->>User: Consent (if required)
OpenIDProvider-->>ClientApp: ID Token + 🔑 Access Token
ClientApp->>ClientApp: Validate ID Token
ClientApp-->>User: User logged in
📊 OAuth vs SAML vs OIDC Comparison
| Feature | OAuth | SAML | OIDC |
|---|---|---|---|
| Primary Use | Authorization | Enterprise SSO | Authentication |
| Format | JSON/JWT | XML | JSON/JWT |
| Complexity | Medium | High | Low |
| Modern Apps | Yes | Limited | Yes |
| Mobile Support | Good | Limited | Excellent |

Comments