3 min to read
ELK Stack Implementation Guide
Learn how to implement ELK Stack (Elasticsearch, Logstash, Kibana) for log management and analysis.
Overview
This guide explores the implementation of ELK Stack (Elasticsearch, Logstash, Kibana) for log collection, processing, and analysis.
What is ELK Stack?
ELK Stack combines three main components: Elasticsearch, Logstash, and Kibana. Recently, EFK Stack (with Fluentd) has also become popular as a lighter alternative.
Architecture(ELK Stack)
Log Pipeline:
Metric Pipeline:
APM Pipeline:
EFK Stack Log Pipeline:
🧩 Key Components
Elasticsearch
- Search engine for storing and searching log data
- RESTful engine for distributed search and analytics
Logstash
- Data processing pipeline for log collection and transformation
- Supports various input sources and output destinations
- Data filtering and transformation capabilities
Kibana
- Data visualization and analysis tool
- Dashboard creation and management
- Log search and analysis interface
Filebeat
- Log file collector
- Lightweight log shipping agent
- Minimal server resource usage
Implementation Guide
Installation Overview
We used the Helm Chart that was archived on May 16, 2023, and installed it in Single Mode for our internal development server.
Installation Methods
1️⃣ Using Archived Helm Charts
Reference repository
- https://github.com/elastic/helm-charts
Implementation reference
- https://github.com/somaz94/helm-chart-template/tree/main/k8s-service/monitoring/elk-stack
2️⃣ Using Latest Version (ECK Operator)
For the latest version, use the ECK operator:
- https://github.com/elastic/cloud-on-k8s/tree/main/deploy/eck-operator
- https://www.elastic.co/guide/en/cloud-on-k8s/current/k8s-install-helm.html
Installation Order
Install components in the following order:
- Elasticsearch
- Kibana
- Logstash
- Filebeat
Configuration Examples
filebeat-values.yaml
filebeatConfig:
filebeat.yml: |
filebeat.inputs:
- type: log
paths:
- /usr/share/filebeat/app/somaz/dev/app/logs/* # Mounted log path
- /usr/share/filebeat/app/somaz/dev/app/logs/**/*
fields:
log_source: "dev-somaz-app" # This becomes Elasticsearch index name
environment: "dev"
app: "somaz"
component: "app"
fields_under_root: true
json.keys_under_root: true # Promote JSON fields to root level
json.add_error_key: true # Add error field on JSON parsing failure
json.expand_keys: true # Expand nested JSON strings
processors:
- decode_json_fields:
fields: ["data"]
process_array: true
max_depth: 2
target: ""
overwrite_keys: true
- script:
lang: javascript
source: |
function process(event) {
// JSON processing logic
return event;
}
logstash-values.yaml
logstashPipeline:
logstash.conf: |
input {
beats {
port => 5044
}
}
filter {
if [log_source] {
mutate {
add_field => { "index_name" => "%{log_source}" }
}
}
# Additional processing configurations...
}
output {
elasticsearch {
hosts => ["https://elasticsearch-master:9200"]
user => "${ELASTICSEARCH_USERNAME}"
password => "${ELASTICSEARCH_PASSWORD}"
ssl_certificate_verification => true
cacert => '/usr/share/logstash/config/certs/ca.crt'
index => "%{index_name}"
}
}
Verification
After setup, verify the installation:
# Check Elasticsearch indices
curl -k -u "elastic:password" "http://elasticsearch.somaz.link/_cat/indices?v"
# Sample output:
health status index uuid pri rep docs.count docs.deleted store.size pri.store.size
yellow open .kibana-event-log-8.5.1-000002 0YwfADLHQryK5bYlBpBm5Q 1 1 0 0 225b 225b
yellow open dev-somaz-app 9zip7n0sdfasdfsadfsdfsdaf 1 1 24161 0 6.5mb 6.5mb
And if Kibana creates a discover that fits the index, it can be checked as follows.
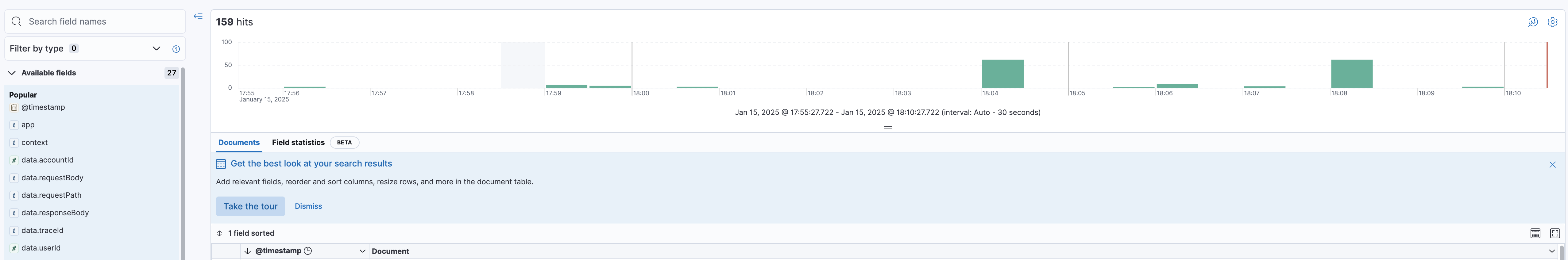
⚠️ Important Considerations
- Elasticsearch Health Status
- Single node clusters can operate safely with yellow status
- Green status is recommended for multiple node clusters
# multiple node cluster will be green clusterHealthCheckParams: "wait_for_status=green&timeout=1s" # single node cluster will be yellow clusterHealthCheckParams: "wait_for_status=yellow&timeout=1s"
- Kibana-Elasticsearch Dependency
- Kibana is completely dependent on Elasticsearch
- Kibana becomes inaccessible if Elasticsearch fails
- Filebeat Load Management
- Full log collection can cause significant load
- Recommend collecting logs from specific pods only
- Operator Installation
- When using the operator, carefully analyze eck-operator-crds
- Follow official documentation for operator setup

Comments